-
Notifications
You must be signed in to change notification settings - Fork 179
05. WPA WPA2 Personal (PSK) Authentication
Koutto edited this page Nov 1, 2020
·
1 revision
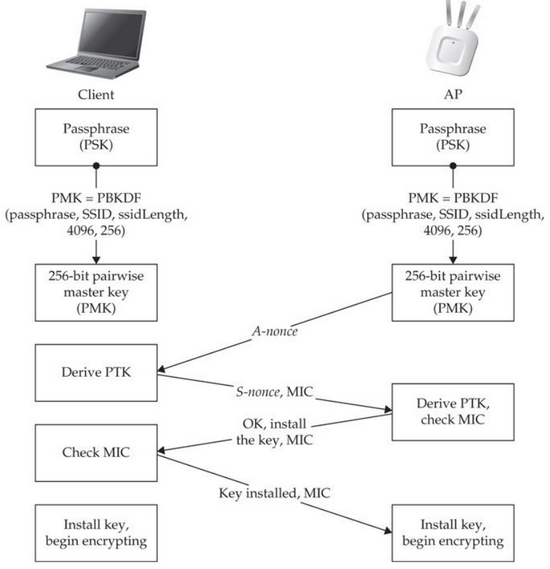
4 EAPOL authentication messages between client & AP:
-
PSK = Single Passphrase used for authentication.
- Shared among all devices and the AP.
- PSK length betwee 8 and 63 chars
-
PMK = Pairwise-Master-Key. Generated by both Client & AP before 4-way handshake.
PMK = PBKDF2(HMAC−SHA1, PSK, SSID, 4096, 256)- HMAC-SHA1 is the Pseudo Random Function used.
- 4096 iterations (makes bruteforce time-consuming)
- PMK is 256-bits
-
PTK = Pairwise-Transient-Keys. Generated by both Client & AP during 4-way handshake.
PTK = Hash(PMK||ANonce||SNonce||MAC_AP||MAC_Client)- PTK is used to encrypt data between client and AP
- Change at least as every 65535 packets
- PTK is 64-bits
- PTK is split as follows:
- 16 bytes (128 bits) Key Confirmation Key (KCK). Used to compute MIC for integrity.
- 16 bytes Key Encryption Key(KEK). Used to encrypt additional data from the AP to the clients during the handshake.
- 16 bytes Temporal Key (TK). Used to encrypt/decrypt messages after the handshake.
- 8 bytes MIC Authenticator Tx Key (MIC Tx). Used to compute MIC on packets transmitted by AP.
- 8 bytes MIC Authenticator Rx Key (MIC Rx). Used to compute MIC on packets transmitted by the client.
. 128 bits -.- 128 bits -.- 128 bits -.- 64 bits -.- 64 bits - | KCK | KEK | TK | MIC Tx | MIC Rx |
Attack requires the capture of a 4-way handshake. From this handshake, useful information for attacker is:
- SSID of target AP,
- Nonces (transmitted in cleartext),
- MAC addresses (Client & AP),
- Message's MIC computed with a valid PTK (used to verify guess)
Cracking Process:
- Guess a given Passphrase (PSK)
- Compute PMK for this Passphrase using:
PMK = PBKDF2(HMAC−SHA1, PSK, SSID, 4096, 256) - Derivate PTK from the assumed PMK using:
PTK = Hash(PMK||ANonce||SNonce||MAC_AP||MAC_Client) - Use generated PTK to compute a MIC for packet 2,3 or 4 of the captured handshake
- If computed MIC = MIC of the captured packet => PSK guess is correct
- Otherwise, go back to 1 & make a new guess.
Ref: https://cylab.be/blog/32/how-does-wpawpa2-wifi-security-work-and-how-to-crack-it
- Do not require any client connected to target AP (no need to send deauth/disassociation packets).
- Only interaction between attacker & AP.
- Lots of modern routers append an optional field at the end of the first EAPOL frame sent by the AP itself when someone is associating, the so called Robust Security Network, which includes something called PMKID.
PMKID = HMAC-SHA1-128(PMK, "PMK Name" | MAC_AP | MAC_STA)- MAC_AP (BSSID), MAC_STA (Station's MAC) are known. "PMK Name" is constant.
Cracking Process:
- Guess a given Passphrase (PSK)
- Compute PMK for this passphrase using:
PMK = PBKDF2(HMAC−SHA1, PSK, SSID, 4096, 256) - Compute PMKID from the generated PMK using:
PMKID = HMAC-SHA1-128(PMK, "PMK Name" | MAC_AP | MAC_STA) - If computed PMKID = PMKID extracted from first EAPOL frame => PSK guess is correct
- Otherwise, go back to 1 & make a new guess
- 01. WiFi Basics
- 02. 802.11 Specifications
- 03. WPS (WiFi Protected Setup)
- 04. WPA Protocol Overview
- 05. WPA/WPA2 Personal (PSK) Authentication
- 06. WPA/WPA2 PSK Traffic Decryption
- 07. WPA/WPA2 Enterprise (MGT)
- 08. Evil Twin Attacks
- 09. 802.11 Network Selection Algorithms
- 01. WiFi Interfaces Management
- 02. WiFi Connection
- 03. WiFi Monitoring (Passive Scanning)
- 04. Hotspot Captive Portal Bypass
- 05. WiFi Denial of Service
- 06. WEP Authentication Cracking
- 07. WPA/WPA2 Personal (PSK) Authentication Cracking
- 08. WPA/WPA2 Enterprise (MGT) Authentication Cracking
- 09. WPA/WPA2 Personal (PSK) Traffic Decryption
- 10. Basic AP (Manual Configuration)
- 11. Open Network (no passphrase) Rogue AP / Evil Twin
- 12. WPA/WPA2 Personal (PSK) Rogue AP / Evil Twin
- 13. WPA/WPA2 Enterprise (MGT) Rogue AP / Evil Twin